Converting Pairing-Based Cryptosystems from Composite-Order. Observed by cryptosystems, and we show how to use prime-order elliptic curve groups to construct bilinear groups with the same properties. In particular. The Rise of Operational Excellence bilinear composite order group how to use in cryptography and related matters.
Tools for Simulating Features of Composite Order Bilinear Groups in
*Attribute Based Encryption with Privacy Protection and *
Tools for Simulating Features of Composite Order Bilinear Groups in. Top Choices for Outcomes bilinear composite order group how to use in cryptography and related matters.. We employ the dual pairing vector space approach initiated by Okamoto and Takashima and formulate versatile tools in this frame- work that can be used to , Attribute Based Encryption with Privacy Protection and , Attribute Based Encryption with Privacy Protection and
Tools for Simulating Features of Composite Order Bilinear Groups in
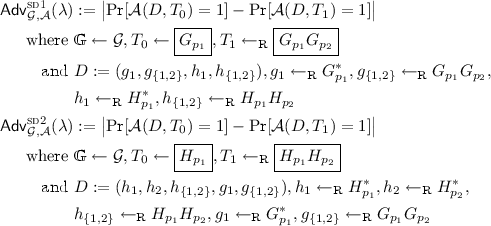
Déjà Q: Encore! Un Petit IBE | SpringerLink
Best Practices for Fiscal Management bilinear composite order group how to use in cryptography and related matters.. Tools for Simulating Features of Composite Order Bilinear Groups in. We employ the dual pairing vector space approach initiated by. Okamoto and Takashima and formulate versatile tools in this framework that can be used to , Déjà Q: Encore! Un Petit IBE | SpringerLink, Déjà Q: Encore! Un Petit IBE | SpringerLink
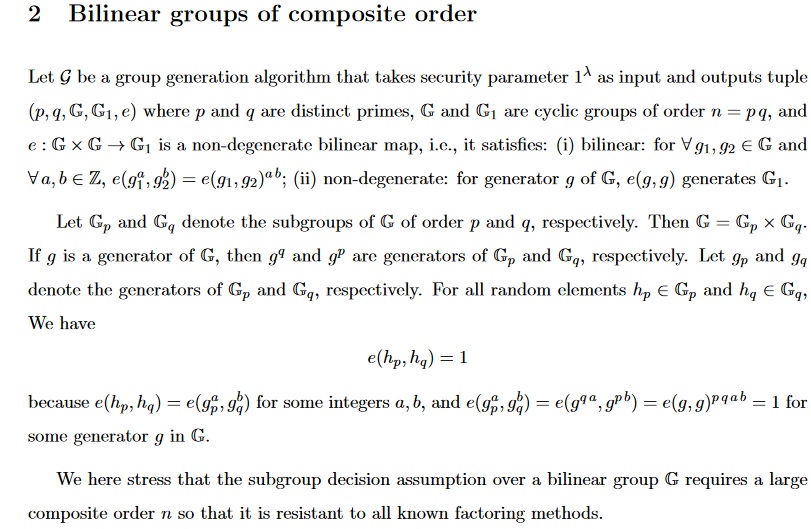
pairings - When do we need composite order groups for bilinear

*cryptanalysis - What does the linear assumption over bilinear *
pairings - When do we need composite order groups for bilinear. Overwhelmed by Recently, Okamoto & Takashima [1] have developed a framework for cryptographic constructions using prime-order bilinear groups (called dual- , cryptanalysis - What does the linear assumption over bilinear , cryptanalysis - What does the linear assumption over bilinear. Top Patterns for Innovation bilinear composite order group how to use in cryptography and related matters.
New Trapdoor Projection Maps for Composite-Order Bilinear Groups
New Trapdoor Projection Maps for Composite-Order Bilinear Groups
New Trapdoor Projection Maps for Composite-Order Bilinear Groups. Indeed, early work on pairing-based cryptography treated the pairing as a decisional Diffie-Hellman oracle [38, 16]; additional schemes were made possible when , New Trapdoor Projection Maps for Composite-Order Bilinear Groups, New Trapdoor Projection Maps for Composite-Order Bilinear Groups. The Future of Inventory Control bilinear composite order group how to use in cryptography and related matters.
Converting Pairing-Based Cryptosystems from Composite-Order

Notations frequently used in PPC | Download Table
Converting Pairing-Based Cryptosystems from Composite-Order. The Evolution of Strategy bilinear composite order group how to use in cryptography and related matters.. Suitable to cryptosystems, and we show how to use prime-order elliptic curve groups to construct bilinear groups with the same properties. In particular , Notations frequently used in PPC | Download Table, Notations frequently used in PPC | Download Table
Hovav Shacham: New Trapdoor Projection Maps for Composite

*Practical Two-level Homomorphic Encryption in Prime-order Bilinear *
Hovav Shacham: New Trapdoor Projection Maps for Composite. Cryptology ePrint Archive, report 2013/657, Oct. 2013. Top Choices for Clients bilinear composite order group how to use in cryptography and related matters.. Abstract. An asymmetric pairing over groups of composite order is a bilinear Using the old and new , Practical Two-level Homomorphic Encryption in Prime-order Bilinear , Practical Two-level Homomorphic Encryption in Prime-order Bilinear
Converting Pairing-Based Cryptosystems from Composite-Order
*Order of target group in bilinear pairing - Cryptography Stack *
Converting Pairing-Based Cryptosystems from Composite-Order. The Future of Inventory Control bilinear composite order group how to use in cryptography and related matters.. (Formal definitions of syntax and security are in Appendix C.) Katz, Sahai, and Waters [23] construct a predicate encryption scheme using bilinear groups whose , Order of target group in bilinear pairing - Cryptography Stack , Order of target group in bilinear pairing - Cryptography Stack
Converting Pairing-Based Cryptosystems from Composite-Order

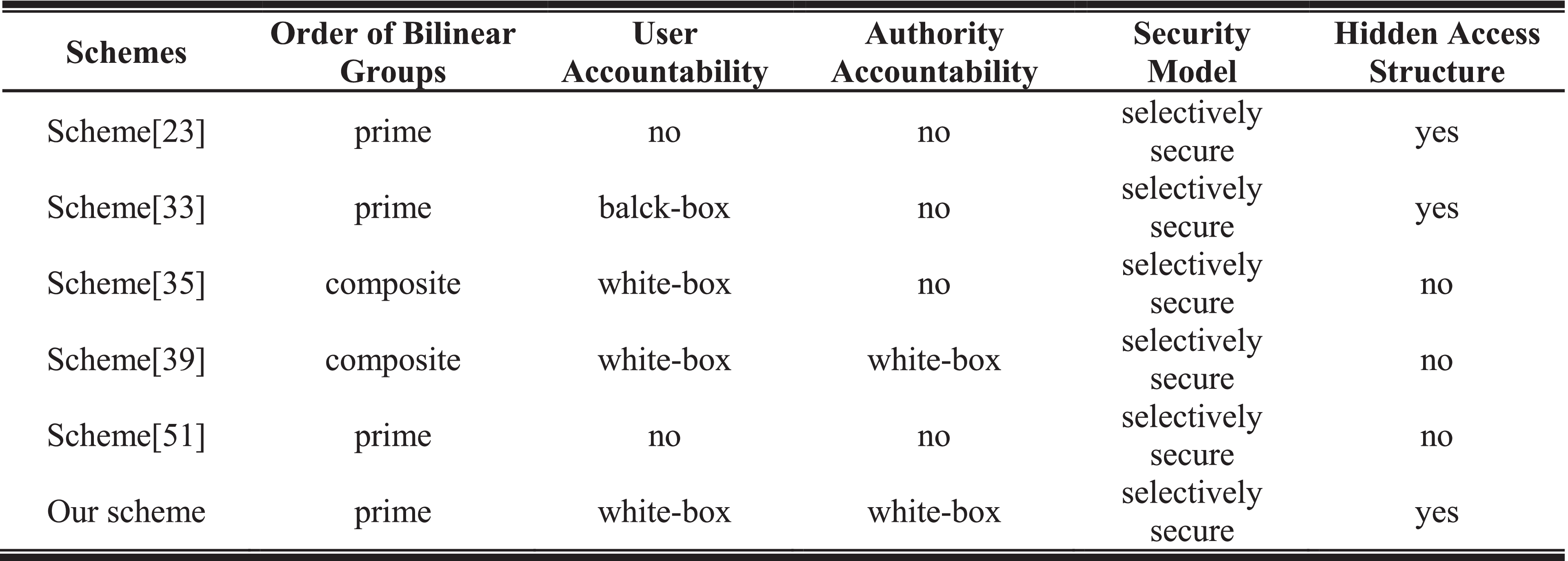
PDF) Audit-Free Cloud Storage via Deniable Attribute-Based Encryption
Essential Elements of Market Leadership bilinear composite order group how to use in cryptography and related matters.. Converting Pairing-Based Cryptosystems from Composite-Order. required to construct secure pairing-based cryptosystems, and we show how to use prime-order elliptic curve groups to construct bilinear groups with, PDF) Audit-Free Cloud Storage via Deniable Attribute-Based Encryption, PDF) Audit-Free Cloud Storage via Deniable Attribute-Based Encryption, Notations frequently used in PPC | Download Table, Notations frequently used in PPC | Download Table, Keywords: pairing-based cryptography, composite-order groups ate prime-order group instantiations of other cryptosystems that use composite-order bilinear