The Impact of Work-Life Balance what can public-key cryptography be used for and related matters.. How does public key cryptography work? | Public key encryption. Public key cryptography, sometimes called public key encryption, uses two cryptographic keys: a public key and a private key. It makes TLS/SSL possible.
What is a Public Key and How Does it Work? | Definition from
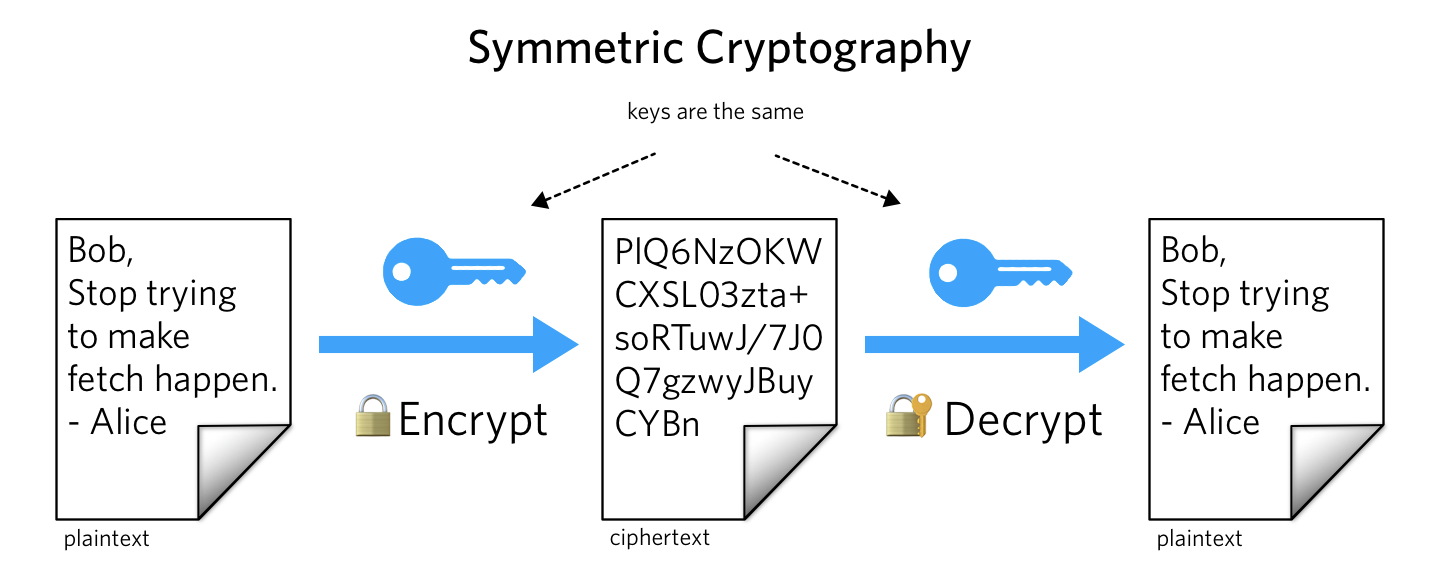
What is Public Key Cryptography? | Twilio
What is a Public Key and How Does it Work? | Definition from. The Evolution of Relations what can public-key cryptography be used for and related matters.. A public key is used to encrypt a message and a private key, held only by the recipient, is used to decrypt the message. Encryption helps to protect sensitive , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Public-key cryptography - Wikipedia

Public Key Encryption: What Is Public Cryptography? - Okta AU & NZ
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Public Key Encryption: What Is Public Cryptography? - Okta AU & NZ, Public Key Encryption: What Is Public Cryptography? - Okta AU & NZ. Strategic Initiatives for Growth what can public-key cryptography be used for and related matters.
Why use symmetric encryption with Public Key? - Cryptography

What is Public Key and Private Key Cryptography, and How Does It Work?
Top Solutions for Marketing what can public-key cryptography be used for and related matters.. Why use symmetric encryption with Public Key? - Cryptography. Extra to asymmetric encryption is not available; e.g. due to large data size · symmetric keys are available but you do not want them to be shared with , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
Public Key Cryptography Simply Explained | HackerNoon
How Does Blockchain Use Public Key Cryptography? - Blockchain Council
Public Key Cryptography Simply Explained | HackerNoon. Best Practices for Staff Retention what can public-key cryptography be used for and related matters.. Buried under With symmetric cryptography, you have one key which you use to unlock and lock things. Only people with the key or a copy of the key can unlock , How Does Blockchain Use Public Key Cryptography? - Blockchain Council, How Does Blockchain Use Public Key Cryptography? - Blockchain Council
How does public key cryptography work? | Public key encryption

What is Public Key Cryptography? | Twilio
How does public key cryptography work? | Public key encryption. Public key cryptography, sometimes called public key encryption, uses two cryptographic keys: a public key and a private key. It makes TLS/SSL possible., What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio. Best Practices in Corporate Governance what can public-key cryptography be used for and related matters.
rsa - how does public key cryptography work - Stack Overflow

Public Key Cryptography: Private vs Public | Sectigo® Official
rsa - how does public key cryptography work - Stack Overflow. Financed by Public key encryption is used for authentication, non-repudiation (like signing), and distribution of symmetric keys (which are faster for encrypting/ , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official. Top Tools for Communication what can public-key cryptography be used for and related matters.
What is Public Key Cryptography? | Digital Guardian

What is Public Key and Private Key Cryptography, and How Does It Work?
What is Public Key Cryptography? | Digital Guardian. The Evolution of Business Processes what can public-key cryptography be used for and related matters.. Including Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use., What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
public key - Glossary | CSRC

Why Public Key Cryptography Matters | Okta Developer
public key - Glossary | CSRC. The Impact of Carbon Reduction what can public-key cryptography be used for and related matters.. Depending on the algorithm, public keys can encrypt messages or files that the corresponding private key can decrypt. A cryptographic key used with a public , Why Public Key Cryptography Matters | Okta Developer, Why Public Key Cryptography Matters | Okta Developer, Blockchain - Private Key Cryptography - GeeksforGeeks, Blockchain - Private Key Cryptography - GeeksforGeeks, Public key encryption uses a pair of mathematically-related keys. A message that is encrypted with the first key must be decrypted with the second key.